A Keras model may contain a "Lambda" layer, which contains embedded Python code in binary format. This code may contain malicious instructions which will be executed when the model is loaded.
The Keras v3 format is the latest format used by TensorFlow and Keras to store ML models.
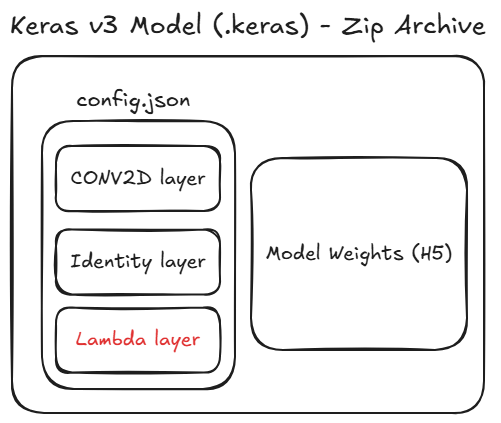
Internally, this format is a ZIP archive which contains a JSON file called config.json which specifies the configuration of the ML Model.
The Model Configuration specifies all the layers of the model, and may specify a Lambda layer.
The Lambda layer specifies custom operations defined by the model author, which are defined simply by a raw Python code object (Python Bytecode).
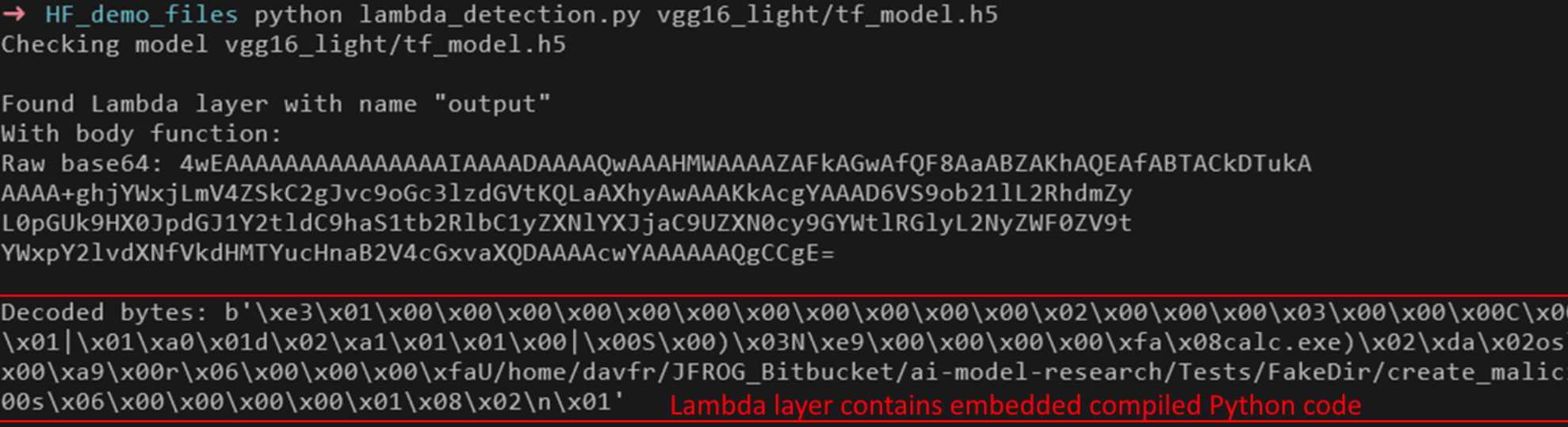
Since arbitrary Python Bytecode can contain any operation, including malicious operations, loading an untrusted Keras v3 Model is considered to be dangerous.
[v] Model Load
[] Model Query
[] Other
To safely determine if the suspected Keras v3 model contains malicious code -
- Extract and parse the
config.jsonfile from the Keras v3 model zip archive, to identifyLambdalayers - Extract and decode the Base64-encoded data of the
Lambdalayer to obtain a Python code object - Decompile the raw Python code object, ex. using pycdc
- Examine the decompiled Python code to determine if it contains any malicious instructions
JFrog conducts extraction, decompilation and detailed analysis on each Keras v3 model in order to determine whether any malicious code is present.