ImageMagick’s CVE-2025-53101 was recently rated Critical with a 9.8 CVSS score by NVD. While the actual impact depends on how the library is used, our analysis revealed additional, more concerning vulnerable commands in the package that had not been published.
CVE-2025-53101 has been disclosed by the ImageMagick team, which may result in denial of service and potentially arbitrary code execution. The vulnerability allows attackers to trigger a stack buffer overflow by processing images with maliciously crafted filenames containing consecutive format specifiers.
The vulnerability results from incorrect offset calculation when processing the image’s filename in the InterpretImageFilename() function in MagickCore/image.c. The code assumes that when processing consecutive format specifiers, each specifier replacement will be exactly 4 characters (like "%03d"), when in reality, the accumulated offset size varies (like "%d").
The offset miscalculation leads to data being written in the wrong location, which may cause data destruction or buffer underwrite, resulting in data being written before the buffer, which may result in memory corruption, leading to denial of service and potentially remote code execution.
Exploitation requires the attacker to supply a file name input with multiple consecutive format specifiers (%d, %o, or %x). For each format specifier, the offset variable used by InterpretImageFilename() accumulates the wrong offset, causing the formatted filename to be written at a bigger offset from the buffer.
Our analysis has discovered that alongside the mogrify command, which has been disclosed as vulnerable, the main magick tool, together with the commands animate, identify, convert, composite, compare and montage are also vulnerable to exploitation using consecutive %d, %x, or %o format specifiers in the filename. The vulnerability can also be triggered by the direct use of InterpretImageFilename() and other functions.
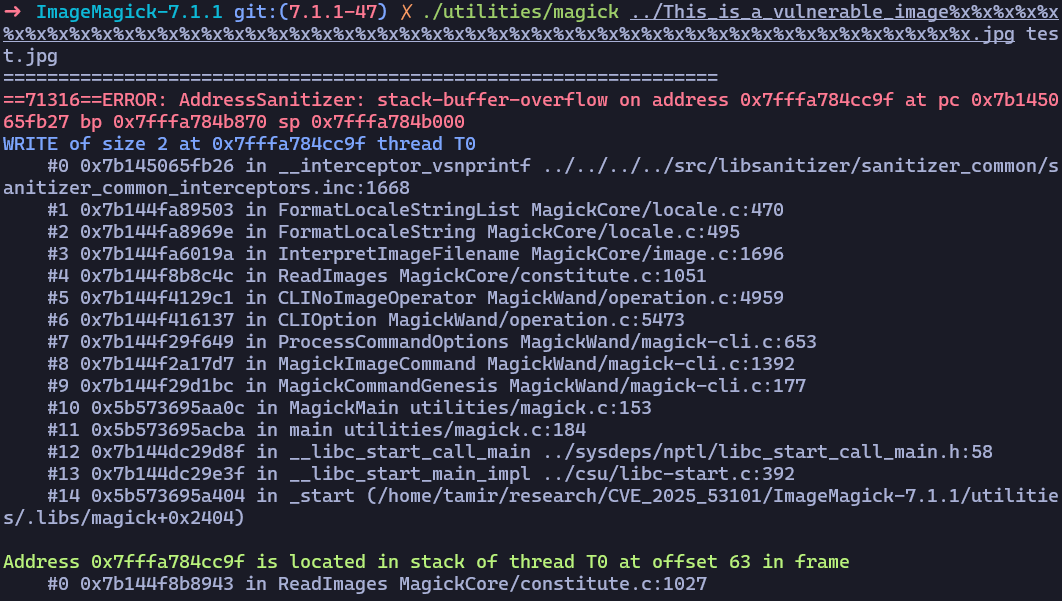
The vulnerability was introduced in version 7.0.7-25 and 6.9.9-37, and it persisted through 7.1.1-47 and 6.9.13-25 respectfully. We strongly recommend upgrading to version 7.1.2-0 or 6.9.13-26, which fixes the issue.